Reply To:
Name - Reply Comment
By Shafraz Farook
Today, life without a phone or a computer is hard to imagine. We are connected on every front and depend on Internet-connected devices for work and in our personal lives. We sign in to at least one online service or application every day, knowing little about the digital footprint we leave or what information we share whenever we post a picture, check in to a venue or send an email.
This seamless integration between man and technology has made us immune to possible vulnerabilities. In the late 90s and the early part of the 2000s, computer viruses were a huge threat. Email scams took centre stage for a while with many unsuspecting computer users falling prey.
Computer hacking has been a threat from the early days of the Internet and in 2016, the world was rocked when the Bangladesh Central Bank was compromised in one of the most public cybercrimes in our region in the time since the computer was invented.
Ransomware is a type of malware—or computer infection—used for data kidnapping, an exploit in which a ‘ransomware criminal’ encrypts a victim’s data until payment for ‘decryption’ is received.
And users at home and in the workplace are under threat from brutal ransomware attacks. Loss of access to critical files, followed by a demand for payment, can cause massive disruption to a user’s or even an entire organisation’s productivity. But what does a typical attack look like? And what security solutions should be in place to give the best possible defence?
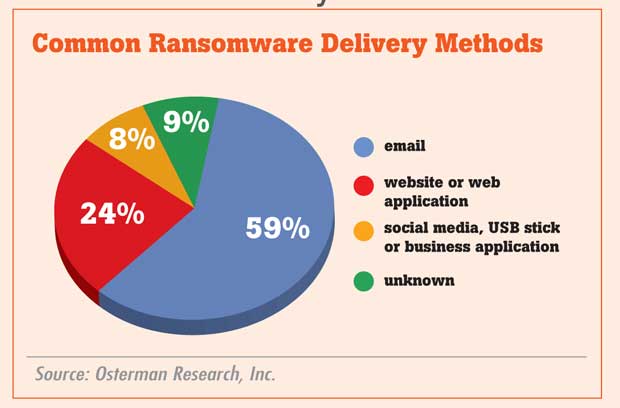
According to Osterman Research, Inc., from June 2015 to June 2016, e-mails with malicious links and attachments represented 59 percent of ransomware infections. To put it differently, potential victims are more than twice as likely to be infected by clicking something in an email than visiting a website soaked with malware-laden advertisements.
In a June 2016 survey from Osterman Research, one out of every two participants indicated that their organisation had suffered at least one ransomware attack in the past 12 months. Moreover, just four percent of respondents from organisations—from a technologically-developed country like the United States—said they were very confident in their current security’s ability to prevent a future attack.
With criminals flocking to ransomware as a source of cheap and easy income, ransomware authors have scrambled to meet the demand. According to Trend Micro, 50 new ransomware families were discovered in the first five months of 2016. That’s easily on pace to surpass the 100 new ransomware families that Symantec said were discovered in 2015.

Ransomware behaviour and contingency plans
Once ransomware is executed in a system, it can either lock the computer screen or in the case of crypto-ransomware, encrypt important files.
For such reasons, ransomware is a great example of why backups are essential. After all, if an individual’s files are only stored in one computer system, ransomware that infects that computer could encrypt them all and restrict access—or even delete them entirely.
Personal and commercial users are encouraged to regularly backup their files to an external hard drive or a remote file storage server. For users running Microsoft’s licensed Windows platform, an automated backup solution called ‘System Restore’ is featured. For Apple’s Macintosh platform, users are encouraged to utilize ‘Time Machine’.
Alternatively, users could backup their personal files to a location where they can’t be ‘written-over’ or erased. For example, placing them on a removable hard drive or uploading them to a cloud-based platform, such as One Drive and Google Drive. Future ransomware could potentially encrypt the files on your connected backup drive or on your network share if you have full write access. As a result, storing backups on an internal hard drive or network may not be enough unless users can encrypt them using encryption tools such as Windows BitLocker or VeraCrypt.
Should users’ files become locked by ransomware and they don’t have the appropriate backups, they could recover them with ShadowExplorer. The tool retrieves ‘Shadow Copies, which Windows uses for System Restore—and will often contain some personal files.
Avoiding ransomware
Aside from using a legitimate backup strategy, users at home and in the workplace can avoid ransomware in the same way they might avoid other forms of malware.
First, one should refrain from downloading or running suspicious and unrecognized files. Ransomware often arrives in executable files attached to emails, malware-laden advertisements on illicit pirate websites or in downloads via peer-to-peer networks. Hence, users should be on high alert and exercise caution over the files they might download or run on their systems.
Second, installing only genuine software can provide extra layers of protection from ransomware, frequent security updates and patches included. Unlicensed software prevents such support from manufacturers and, may even contain dangerous malware. Users should also keep their software updated. In particular, using an old version of a web browser, operating system or a browser plugin can allow for ransomware to be installed through open security holes.
Unfortunately, encryption is just the beginning—ransomware criminals are expected to raise the bar. Just recently, ransomware attacks had been directed at servers and databases with the intention of causing more widespread damage to critical services and systems. For example, MongoDB, a free and open-source database system, runs on a range of platforms including Red Hat, SUSE, Amazon Linux, and Ubuntu—as well as Windows systems. In January, ransomware groups had deleted over 30,000 MongoDB databases and exposed over 680 TB of data– significantly more difficult to recover from!